Category: Web
Difficulty: Very Easy
Description: During Pandora’s training, the Gunhead AI combat robot had been tampered with and was now malfunctioning, causing it to become uncontrollable. With the situation escalating rapidly, Pandora used her hacking skills to infiltrate the managing system of Gunhead and urgently needs to take it down.
Address: 104.248.169.175:30408
Attachments: web_gunhead.zip
First of all if we visit the site this is what we see:
 On the right there are some buttons that allows us to open some tools, and one of them will open a console-like window:
On the right there are some buttons that allows us to open some tools, and one of them will open a console-like window:
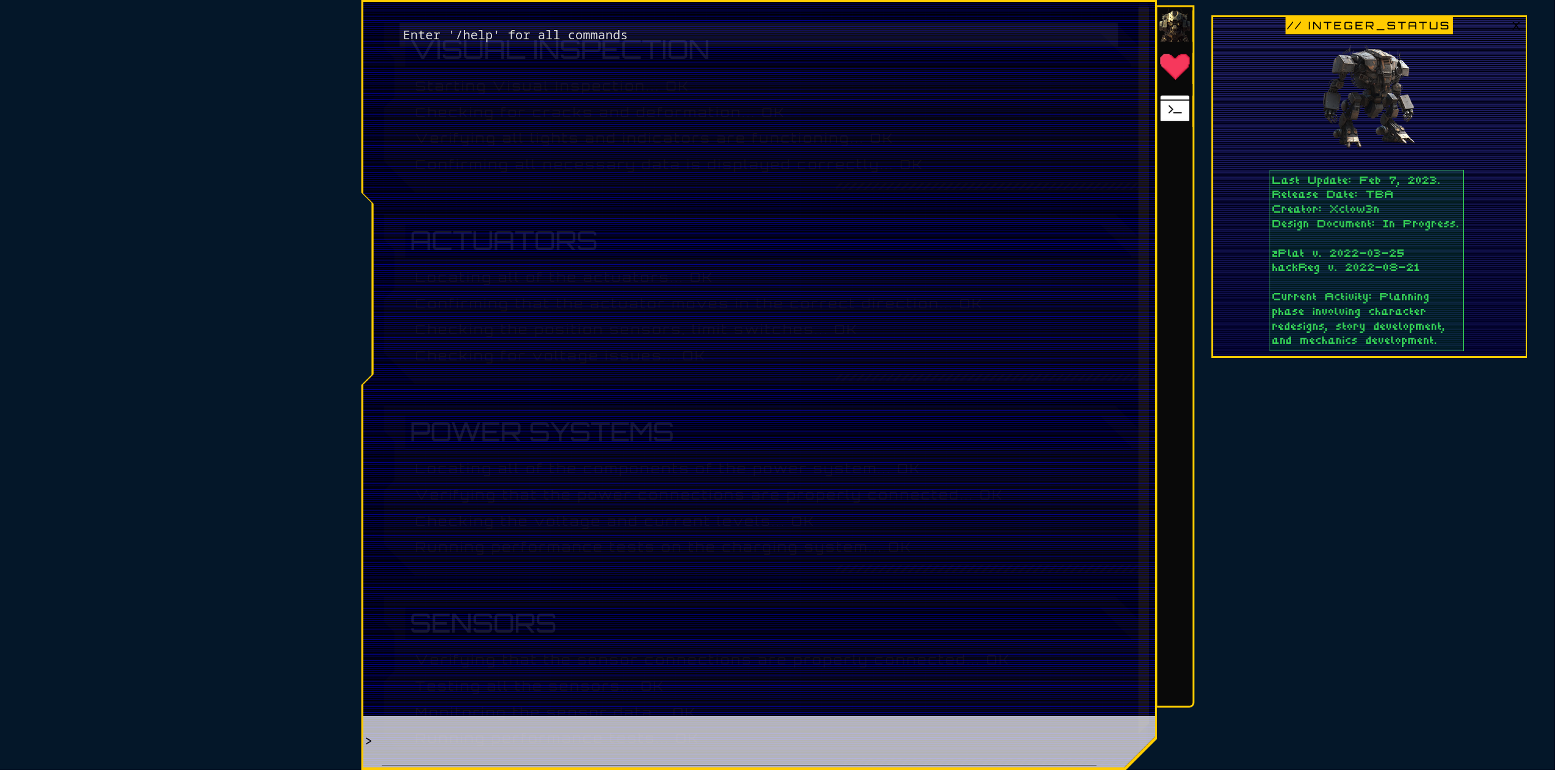 If we enter
If we enter /help we can see the available commands. One of those (the /ping command) asks us to enter also an ip address as input that will be pinged:
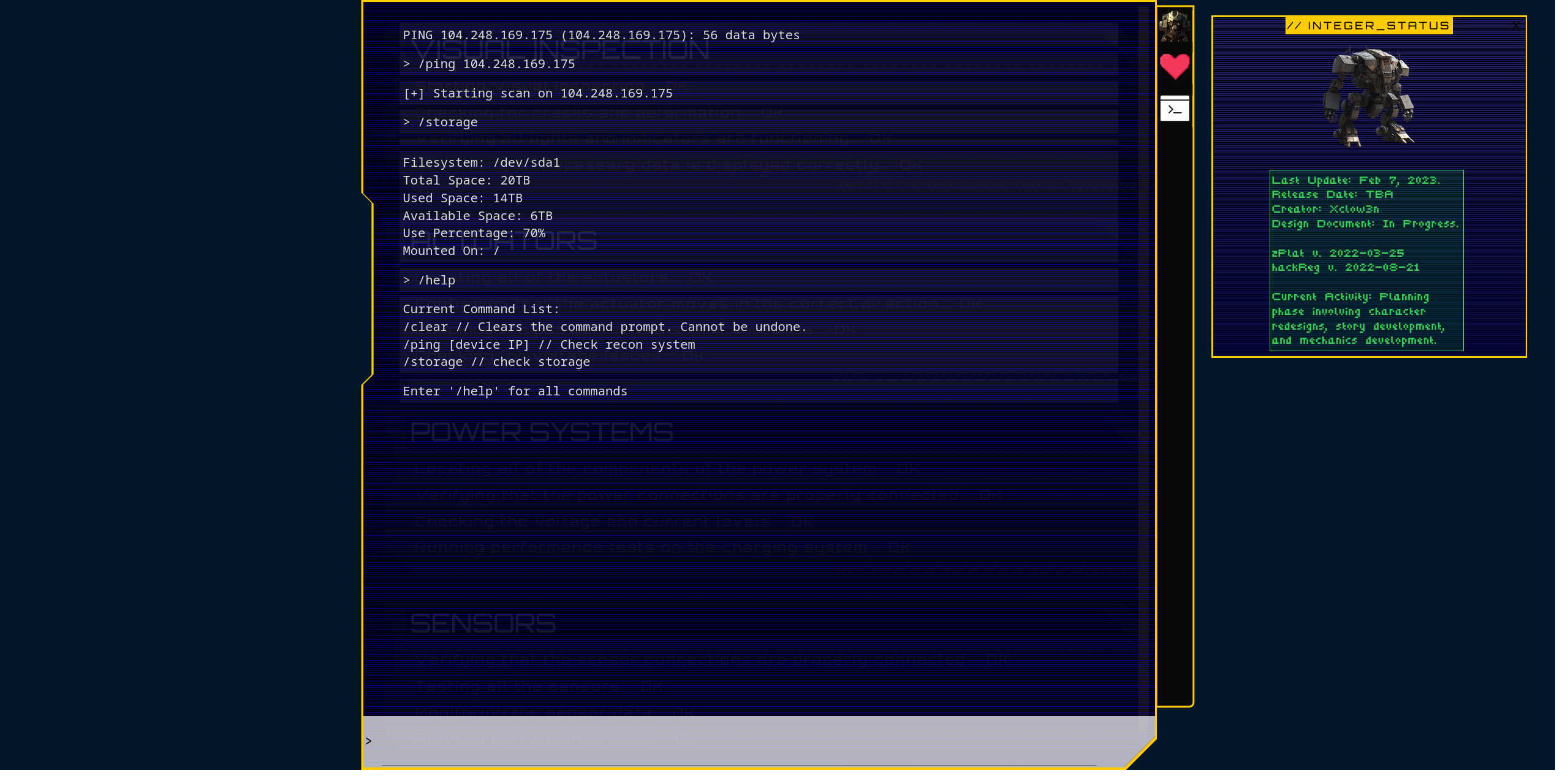 This caught my attention right away since we can provide some additional custom input. But we have also the source code of the app, so let’s see what it really does. After some research I found that the file that handle the behavior of the ping command is
This caught my attention right away since we can provide some additional custom input. But we have also the source code of the app, so let’s see what it really does. After some research I found that the file that handle the behavior of the ping command is challenge/models/ReconModel.php, and in particular the class named ReconModel:
class ReconModel
{
public function __construct($ip)
{
$this->ip = $ip;
}
public function getOutput()
{
# Do I need to sanitize user input before passing it to shell_exec?
return shell_exec('ping -c 3 '.$this->ip);
}
}
From what we can see it executes a ping command and pass to it directly our ip without sanitizing it. Since we have to print the flag (which is located in the /flag.txt file) we can submit to the console a command like /ping ; cat /flag.txt: