Category: Web
Difficulty: Very Easy
Description: Pandora’s latest mission as part of her reconnaissance training is to infiltrate the Drobots firm that was suspected of engaging in illegal activities. Can you help pandora with this task?
Address: 159.65.81.12:30378
Attachments: web_drobots.zip
If we visit the site we will see a login page that asks us for username and password:
Since we have also the source code of the site, let’s take a look. From the Dockerfile we can see that we are talking about a Flask site. From the file web_drobots/challenge/application/blueprints/route.py we can see that, in the /login api endpoint, after some initial checks, the handler for that endpoint calls a function called login, and after that if it returns a user the session is esabilished and access is granted. So let’s see what it does! The source code for that function is located in web_drobots/challenge/application/database.py:
def login(username, password):
# We should update our code base and use techniques like parameterization to avoid SQL Injection
user = query_db(f'SELECT password FROM users WHERE username = "{username}" AND password = "{password}" ', one=True)
if user:
token = createJWT(username)
return token
else:
return False
Since the username and password we provide are directly inserted into the SQL query without any input sanitization we can perform a simple SQL Injection by entering as username " OR 1=1 -- and as password something casual like test (we have to put something because the only check the code does is that username and password must not be empty).
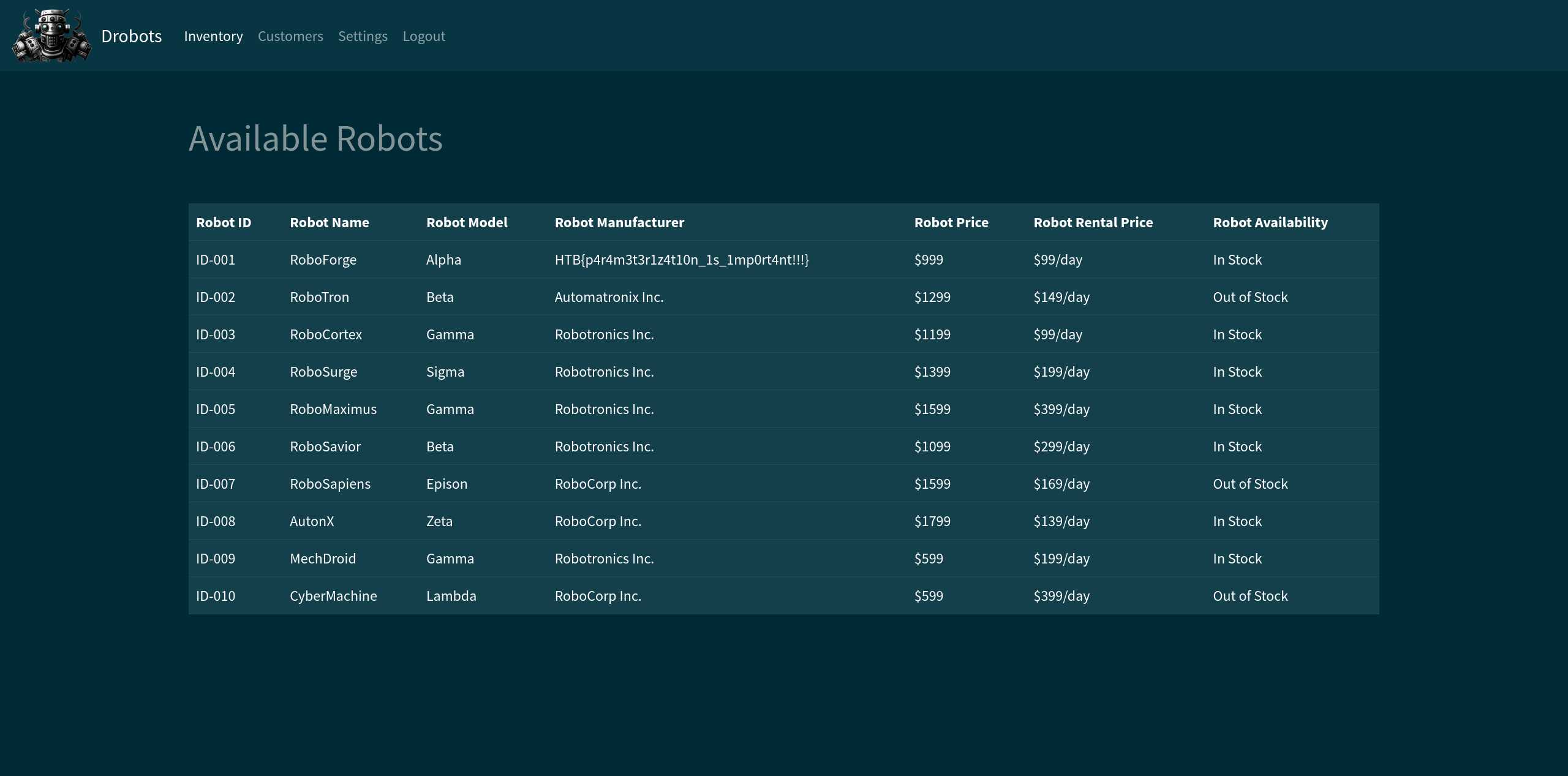
After doing that we successfully logged in and we are being redirected to the /home endpoint, where we can easily spot the flag: